
In today’s digital age, where data and information are the lifeblood of businesses and individuals alike, the importance of cybersecurity cannot be overstated. One of the most menacing threats that organizations and individuals face is the dreaded “Brute Force Attack.“
What is a Brute Force Attack?
A Brute Force Attack is a relentless and straightforward hacking technique used by cybercriminals to gain unauthorized access to a system or an account. Unlike sophisticated hacking methods, which rely on exploiting vulnerabilities or crafting intricate malware, a brute force attack relies on the sheer persistence of the attacker.

The Mechanics Behind a Brute Force Attack
Step 1: Gathering Information
The first step in a brute force attack is reconnaissance. The attacker gathers as much information as possible about the target. This includes identifying the target system, understanding its architecture, and pinpointing potential vulnerabilities.
Step 2: Choosing the Right Tool
Armed with valuable information, the attacker selects a suitable brute force tool or script. These tools are designed to automate the process of trying every possible combination of usernames and passwords until the correct one is found.
Step 3: Launching the Attack
With the chosen tool in hand, the attacker launches the attack. The tool systematically goes through all possible combinations, trying each one until it hits the jackpot. This can be an incredibly time-consuming process, but it can be devastatingly effective if successful.
Step 4: Gaining Unauthorized Access
Once the correct username and password combination is discovered, the attacker gains unauthorized access to the target system or account. From there, they can wreak havoc, steal sensitive information, or cause significant damage.
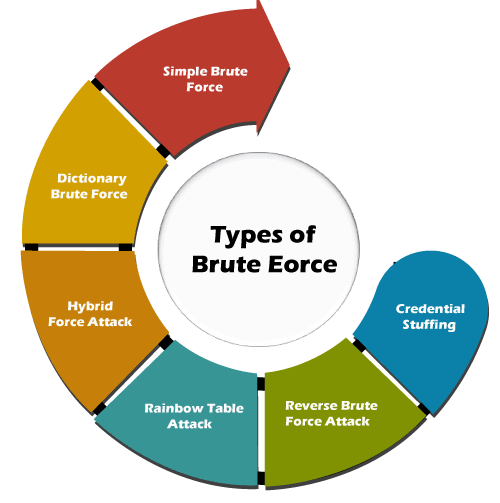
Protecting Against Brute Force Attacks
Now that we understand the mechanics of a brute force attack, it’s essential to know how to protect yourself or your organization against this threat.
Strong Password Policies
Implementing strong password policies is the first line of defense. Encourage users to create complex passwords that include a mix of upper and lower-case letters, numbers, and special characters. Regularly update passwords and avoid using easily guessable combinations.
Account Lockout Policies
Implement account lockout policies that temporarily suspend an account after a certain number of failed login attempts. This makes it significantly more challenging for attackers to gain access through brute force.
Two-Factor Authentication (2FA)
Two-factor authentication adds an additional layer of security by requiring users to provide a second form of verification, such as a one-time code sent to their mobile device. Even if an attacker obtains the correct password, they would still need the second factor to gain access.
Regular Monitoring and Alerts
Implementing real-time monitoring and alerts for suspicious login activity can help detect and respond to brute force attacks promptly.
Final Thoughts:
In the ever-evolving landscape of cybersecurity, understanding the threat of brute force attacks is crucial. By staying vigilant, implementing robust security measures, and educating users about the importance of strong passwords, you can significantly reduce the risk of falling victim to these relentless attacks. Remember, in the world of cybersecurity, prevention is often the best cure.